Okta SSO
cside allows you to create an Okta OIDC application and use it to authenticate users into your cside organization.
When you enable Okta SSO, anyone with your company email domain will be forwarded to authenticate with Okta. This means you can use Okta to scope who can access cside, and when you allow someone, they will automatically be added to your cside organization with no permissions.
Requirements:
- cside Enterprise plan
- Organization Admin role in cside
- An already setup cside organization - the initial admin (you) will be the first user, and will be converted to SSO upon migration.
- Admin access to your Okta account
Navigating to SSO Settings
To access the SSO settings in cside:
- Click on your account at the bottom left corner of the dashboard
- Select View organization
- Select Settings
- Navigate to the SSO tab
Create an Okta OIDC Application
- Go to your Okta Admin console. Head into the Applications > Applications tab.
- Click on the "Create App Integration" button.
- Select "OIDC" for Sign-in method.
- Select "Web Application" for Application type.
- Click Next.
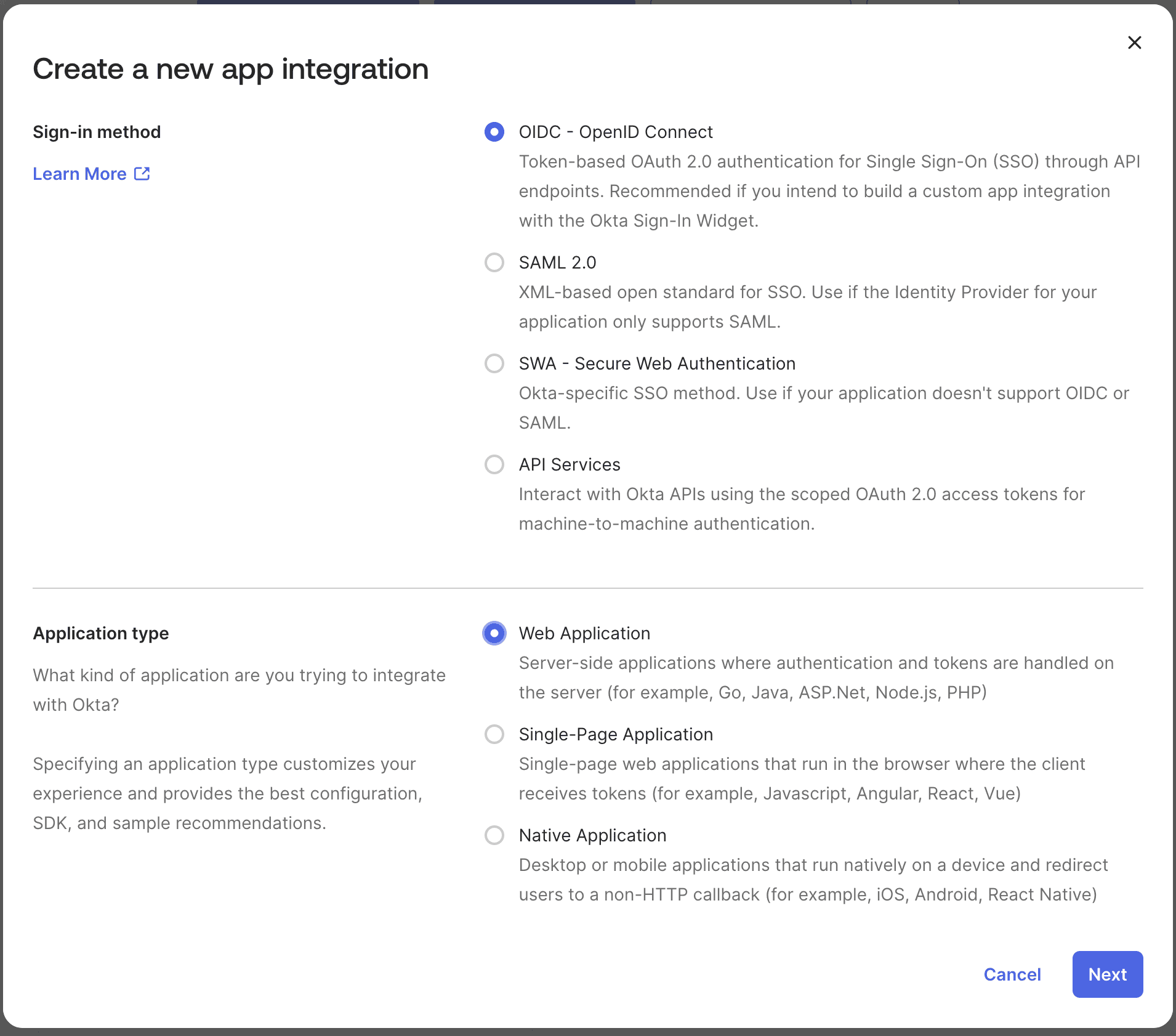
Configure Okta OIDC Application
Now we will configure this application to be compatible with cside.
- Enter the name of the application as "cside"
- Under Grant type, ensure Authorization Code is checked (this is the default)
- For Sign-in redirect URI, enter
https://dash.cside.com/auth/callback/oidc - Clear the Sign-out redirect URI
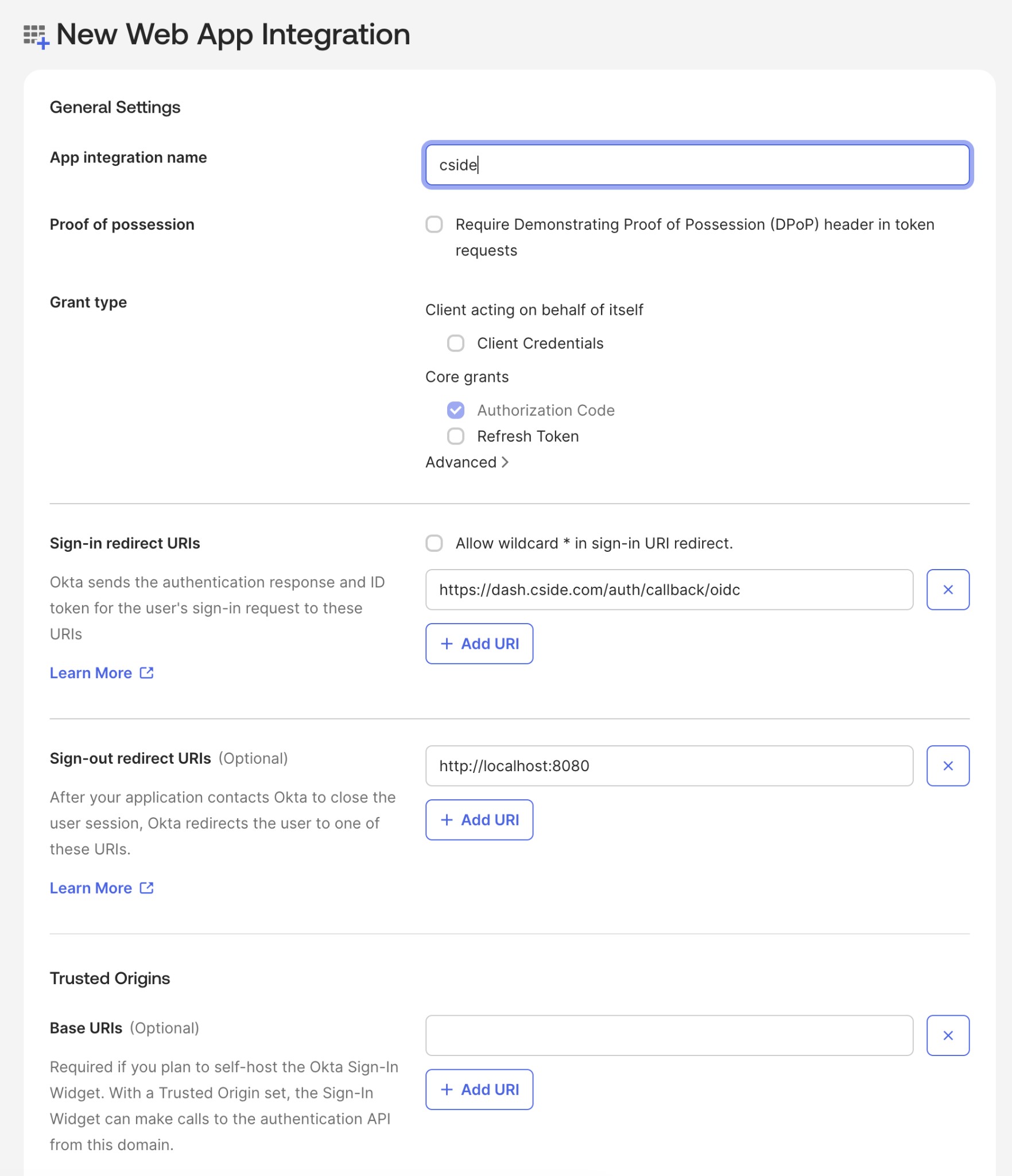
- For assignments, this is largely down to your companies posture on who should have access to cside. For the sake of this example, we will allow anyone in the organization to access. Please think carefully before selecting this option.
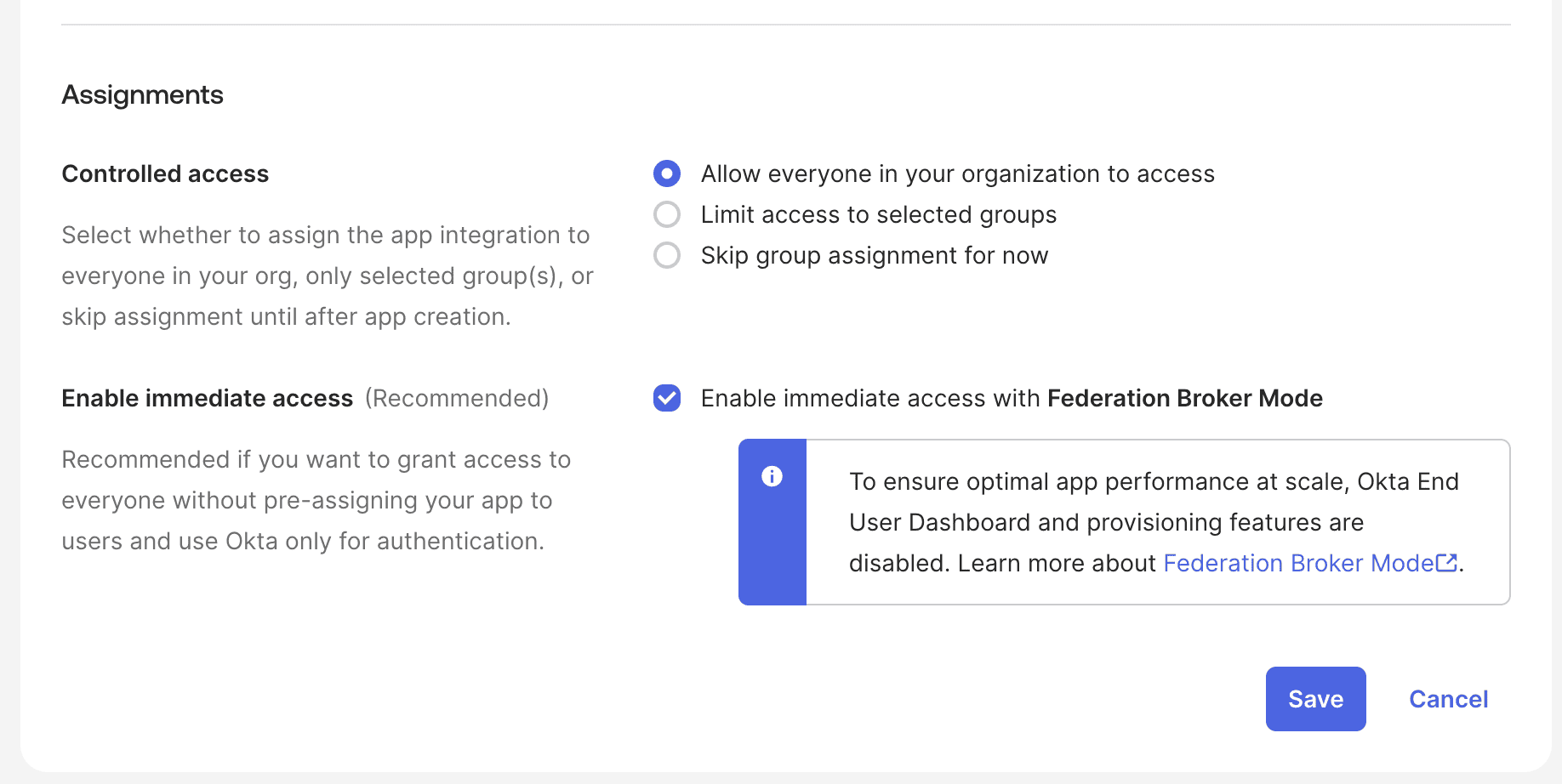
Obtain Required Details
Want to add the cside logo to this application?
Here's the logo ready-to-go in a format Okta supports:
You'll need the following information from your Okta application to configure SSO in cside:
- Client ID: Found in the application settings (e.g.,
0oa1a2b3c4d5e6f7g8h9i) - Client Secret: Found in the application settings
- Okta Endpoint: Your Okta domain (e.g.,
dev-123456.okta.comor your custom domain likeid.yourcompany.com)
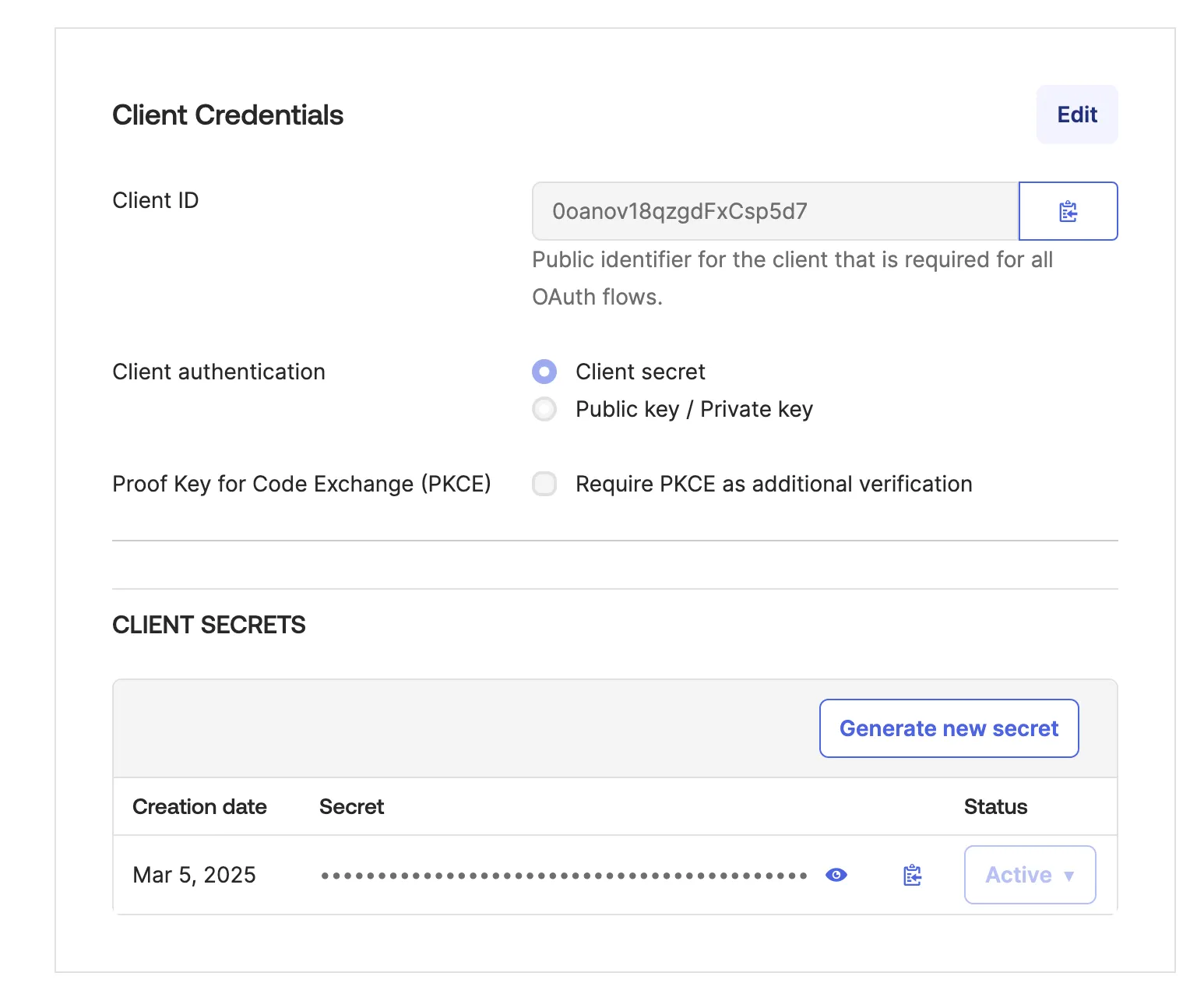
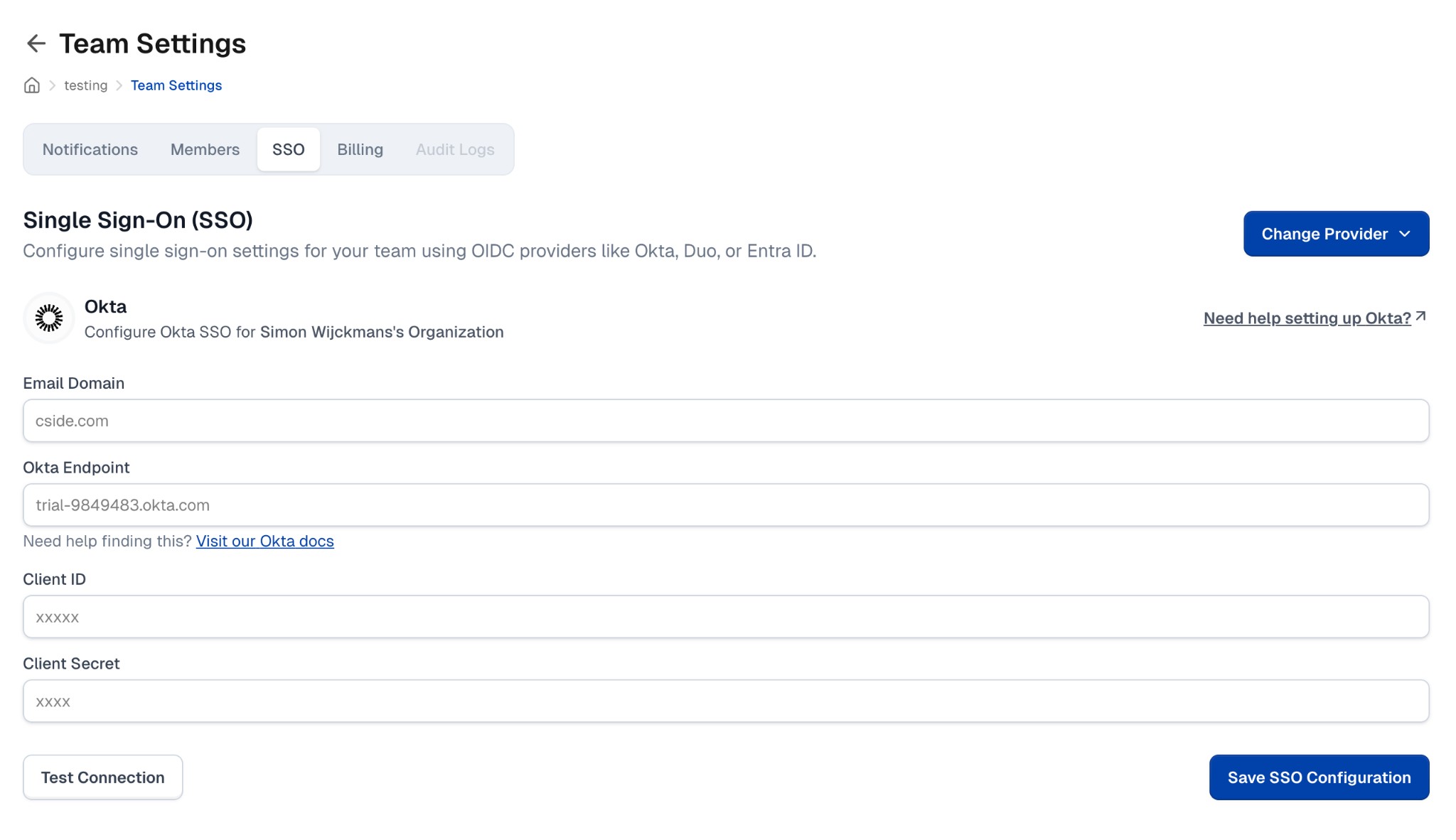
Configure SSO in cside
- Go to the cside dashboard.
- Navigate to the SSO settings as described in Navigating to SSO Settings.
- Click Select Provider (or Change Provider if you already have SSO configured) and select Okta.
- Fill in the required fields:
- Email Domain: Your company's email domain (e.g.,
example.com) - this must match the users in your Okta instance - Okta Endpoint: Your Okta domain (without
https://) - Client ID: The Client ID from your Okta application
- Client Secret: The Client Secret from your Okta application
- Email Domain: Your company's email domain (e.g.,
- Click Test Connection to verify the configuration.
- Once verified, click Save SSO Configuration.
Testing Your Configuration
After saving the SSO configuration, you can test it by:
- Opening a new incognito/private browser window
- Navigating to dash.cside.com
- Entering an email address with your configured domain
- You should be redirected to Okta for authentication
Need Help?
If you encounter any issues during setup, contact your cside representative for assistance.
How is this doc?